
The challenge
The demands on risk and compliance frameworks are increasing rapidly: They absorb resources and require expensive expert knowledge.
Tools can help, but they carry the risk of collateral damage: Complex parameterizations and expensive customizations complicate implementation, impractical and cumbersome operation burden users and risk culture, and last but not least, there is the threat of unreasonable operating costs and operational dependency on external service providers.

The development
The developers of GoCompliant’s ToolSuite have accumulated several decades of specific experience around these challenges.
Therefore, while the concept of the software is based on economic doctrine, the design is the result of countless lessons learned and implemented together with ten thousands of users, while performing over a million control activities and thousands of audit points.

The solution
The result is a software
- that is industry-independent and simple
- that can be integrated smoothly into day-to-day operations
- that can be set up in a simple and linear way
- that does not require a certain methodological approach
- but whose functional power can be called up at any time if required.
Choose from our modules
Our modular design allows to tailor the software precisely to your needs. The modules integrate seamlessly with each other (e.g. in reporting), but also function independently.
By using only the modules you need, you create a customized and comprehensive Governance, Risk & Compliance (GRC) solution that covers your exact needs.
Information Security Management (ISMS)
The ISMS concept can be set up individually or according to standard modules (e.g., ISO standards). A freely configurable workflow engine supports the efficient execution of assessments within the ISMS cycle.

In a first step, the assets inventory is created. Required attributes can be flexibly defined depending on the asset type. Depending on the needs, the objects can be placed in context, for example, through connections
between different assets (to represent dependencies and inheritance logic),
with processes, security incidents, etc.

The analysis of protection needs (e.g., using the CIA criteria) as well as the assignment of threats, vulnerabilities, risks, etc., are set up according to the individual needs of the customer. Alternatively, or additionally, standard selection lists are available (based on ISO/IEC 27001-2022).

Once the risks are identified, they are assessed according to the customer's risk assessment strategy. Our tool offers great flexibility in terms of designing the systematics. Risk assessments to be conducted can be individually defined, and measures or controls can be assigned accordingly.

Various standard overviews provide transparency about the current status quo, such as measures, vulnerabilities, security incidents, and periodically conducted controls. GoCompliant meets the customer's specific information needs through dashboards that combine and visualize relevant data across modules as well.

Dashboards can be configured freely according to individual preferences. The illustration shows one possible solution.
Internal Controls

In a first step, controls are described (title, description, instructions, etc.). Any additional data fields can be used as desired.
Then, in the so-called control plans, it is defined which employees must perform the control and how often.
The software automatically triggers the control tasks based on the control plan. Users are notified of their control tasks by mails, automatically reminded and warned when a task reaches or exceeds its due date.

The system automatically generates control tasks based on the control plans that have been set up. The responsible employee(s) are notified by email that a control task has been generated.
Depending on the setup, the responsible person has the opportunity within a certain time window to perform the control task, to document the execution in the tool, to upload control evidence if necessary and to mark the task as completed.

The results of executed controls can be visualized at any time. Standardized dashboards and predefined or manual queries are available for this purpose. For example, it is possible to monitor whether the control tasks were executed by the employees on time.

Controls can be periodically measured for adequacy, timeliness, and effectiveness as needed. This is done in the form of a separate review task that relates to a specific control.
The person assigned to the review task does not have to be the same as the person performing the control and can, for example, be an employee from a second-line-of-defense function.
Risk-Assessments

Risks are defined and documented in a central register. A set of standard data fields is available, but any additional data fields can be set up and used.
Risks can either apply to the entire organization or only to a part of it.

Risks are typically assessed according to probability of occurrence and extent of damage. Likewise, an inherent (gross) risk and a residual (net) risk are often documented. Our tool is designed to be flexible enough to allow the customer to determine which system should be used for the assessment. Also, different assessment types can be used within the same organization, which differ from each other in the systematics.
When assessing risks, data content of the other modules can be displayed. For example, if a risk is linked to controls, all controls and control results are automatically displayed.

A risk assessment typically concludes by determining whether the risk situation should be accepted or improved with further measures. This is where the link to the "Action Tracking" module comes into play. Further risk-reducing measures are documented in the form of an action, assigned to a responsible person and given a due date (further categorizations etc. are also possible). Now the newly recorded measure (action) appears in the to-do list for the corresponding user.

Periodically, an assessment of risks can be carried out. Such an assessment can be performed either for the entire organization or only for a part of it. Likewise, either all risks from the central risk inventory can be assessed, or only a part of them (if necessary, new risks can also be identified and documented during the assessment).
In this way, different constellations can be mapped. For example, an enterprise-wide Risk and Control Self Assessment (RCSA) or a thematically limited assessment (e.g. IT Risk Assessment) can be carried out.
Action Tracking
Different types of actions can be documented in the tool. These can be actions from internal audit reports, external audit reports, risk & control self-assessments, etc. On one hand, the different types allow different workflows to be defined (e.g. regarding approval of the opening or closing of an action). On the other hand, different user rights can be set up. Evaluations are also possible according to action types.

An action can belong to a report depending on the setup of the action type. This is the case, for example, with internal or external audits. In such a case, the report and its content can be captured in GoCompliant. The findings and/or recommendations made can be recorded and documented as an attribute of the report. The structure of the report can be chosen flexibly. Access rights can also be restricted, so that an action owner cannot read the entire report, for example.

The implementation status of actions can be tracked at any time. This can be done for a single action, but also across a number of actions, e.g. across all actions that originate from the same report. During the implementation period, the action owner is reminded, depending on the configuration request, that the implementation status of an action must be updated regularly. Likewise, the owner is reminded of the action before and, if necessary, after the implementation period has expired.

Just as in the other modules, a variety of evaluation options are also available for Action Tracking. A set of standardized evaluations is available, which can be generated with two clicks. In addition, customer-specific quick evaluations can be configured, which are either called up ad-hoc or generated and delivered automatically, e.g. on a monthly basis.
Document Management (DMS)

All documents can be stored and managed centrally. The documents can be filed in different folders as required and provided with comments.
In the central repository, documents can be easily filtered and searched. The company's employees only have read access to the documents that are relevant to them.
Several language versions are supported per document, and a validity period can be defined for each document version.
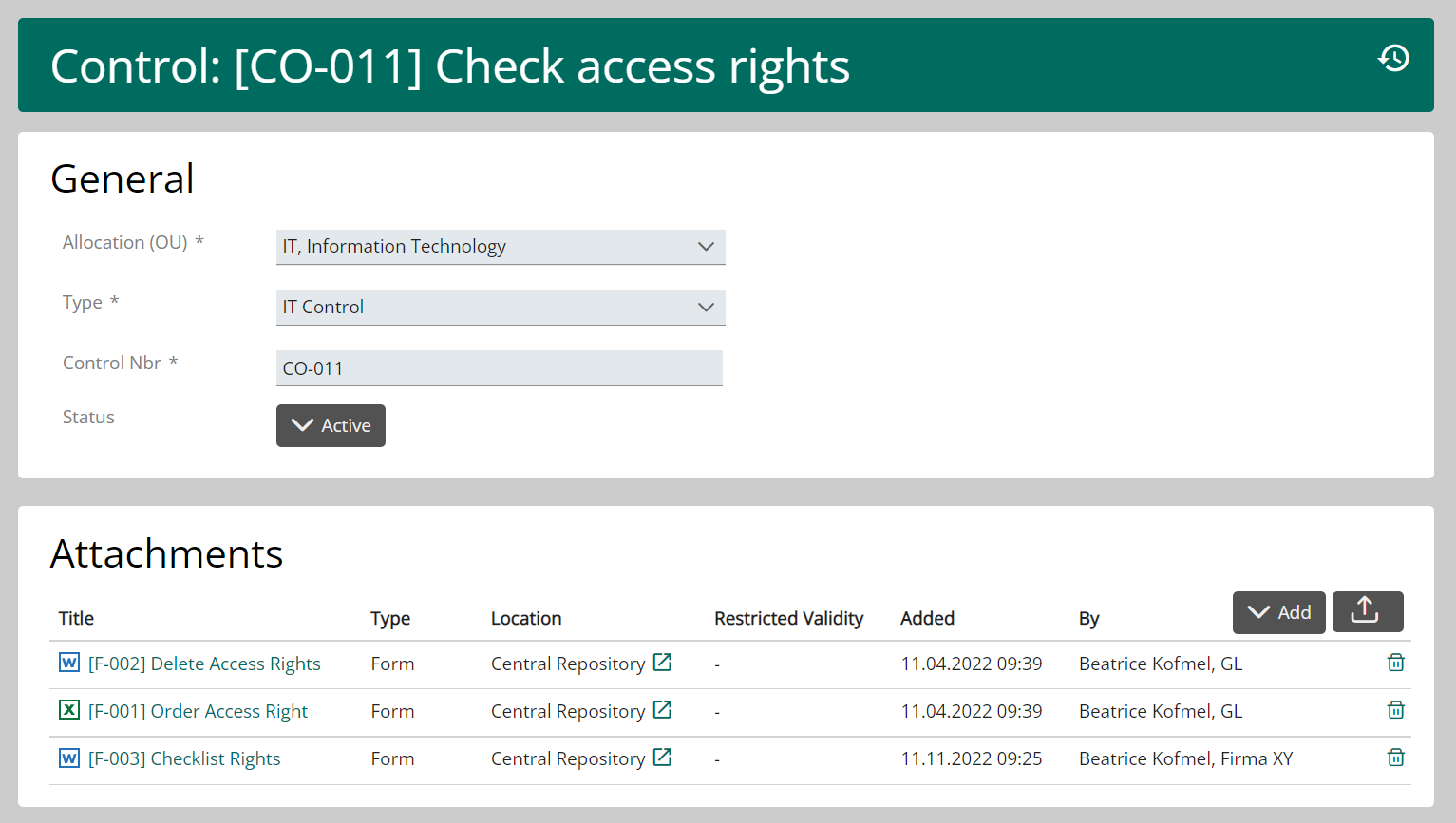
The central documents can be linked at various locations in the application. For example, a policy can be linked to a control. This automatically ensures that the person performing the control can open and read the current version of the policy while performing the control.
Linking is also possible in the risk assessment, and for incidents, risks or processes.

Document maintenance are supported by configurable workflows. For example, new document versions can be verified, changes can be submitted for approval, or new documents can be requested and created.
The adjacent screen shows a possible implementation for the consultation of a new directive. It should be noted that the workflow steps can be set up according to your needs and supplemented with additional fields.
Business Continuity Management (BCM)

The Business Continuity Management (BCM) module is used to ensure the continuity of business-critical products, processes and activities (PPA), including IT services (ITSCM). The module is based on the BSI standard 200-4, which is compatible with the ISO standard ISO 22301 at the "Standard BCM" level. A respective certification can be supported with this module.

In the first step, all relevant products, processes and activities (PPA) are listed and documented. Ideally, an already existing process documentation landscape can be leveraged for that purpose and stored in GoCompliant. Each PPA is then assessed in terms of business criticality in the Business Impact Analysis (BIA).

The Business Impact Analysis (BIA) enables companies to assess the impact of disruptions and disasters on their operational processes, products and activities (PPA). This module supports a comprehensive and structured analysis to identify the key areas that need to be prioritized in the event of a disruption.
Once all critical processes and their dependencies on resources/assets have been identified, a comparison of the Maximum Tolerable Period of Disruption (MTPD) with the Recovery Time Objectives (RTOs) of the assets associated with the PPA is performed for each PPA. In case of inconsistencies, underlying risks are assessed, and initial measures are defined.

The results of the business impact analysis (BIA) and risk analysis provide assessments on criticality, resource dependencies and risks. Based on this information, appropriate Recovery Options can be defined to protect the critical business processes.
This is followed by the definition of individual Business Recovery Plans (BRP), which can be stored as PDF documents and printed out.
Incidents

The module "Incidents" allows to maintain different types of events. Typically, operational losses are recorded, but in addition, e.g. customer complaints, IT incidents or any other event types can be set up.
Any number of data fields can be configured for each event type. For example, in the case of operational losses, the loss amount, any cost center, etc. can be recorded.

For each event type, it is possible to define whether the events are to be recorded by a central instance or decentrally by the employees. Depending on the configuration, a single- or multi-stage approval process then takes place.
As soon as an event is active, it can be added to and updated. As usual, documents can also be attached or linked.

All current events can be monitored via a simple status overview. Extensive search options are also available in this module
Smart Connect

The driving force behind this module is the customer's desire to exploit the potential of digitization. A lot of data is already digitized in the backend systems, but cannot be visualized and used in GoCompliant without a connection.
The module therefore enables the connection of one or more backend systems and thus an automated data flow to GoCompliant.

The data from the backend system can be configured as a source in the control setup and the administrator determines to what extent the detailed data must be evaluated, supplemented and commented during the control execution.
Multiple interfaces/data sources can also be configured for a control.

For example, changes to central configuration tables of a backend system (e.g. SAP) can be collected in GoCompliant, displayed on a monthly basis and individually commented/visualized. Or, as in our screen example, conspicuous transactions can be efficiently verified.
The advantages are obvious: critical changes are discovered quickly and can be corrected if necessary without having to make a review over entire systems or data structures.
Outstanding features
After decades of experience, we know what requirements are needed for GRC software in order to survive in daily operations.
Modular
Pay-what-you-use thanks to our modular design
Configurable
Easy to implement, flexibly extendable and configurable
Industry-neutral
Applicable in the financial industry and all other industries
Direct
Direct involvement of end users and line managers
Intuitive
Comprehensive and clear dashboards
Meaningful
Integrated reporting functionality with individual templates
Integratable
Connectivity (e.g. to SAP) via standardized interfaces
Scalable
Runs as cloud solution (SaaS) or locally (on-premises)
Tech Specs
GoCompliant is a web application with Java Application Server, SQL database and Responsive Design.
| Industry standards | We rely on modern and proven technologies: Web Application, Single Sign-On, SQL Database, Java Application Server, Kubernetes, LDAP. |
| Browser-based | Support for all modern web browsers including mobile devices (Responsive Design). |
| On-Premises / Cloud | You have the choice: on-premises operation at your site or cloud hosting in a CH data center (ISO27001). |
| Single Sign-On | We are happy to connect your Active Directory for secure authentication of users. |
| Feature Requests | We gladly accept customer requests and implement them promptly. We look forward to getting to know your ideas. |